# Setup IDP integration on keycloak
Keycloak can delegate authentication with Identity Brokering on OIDC (OpenID Connect), SAML2.0, Kerberos and with social networks like Google, Github, Facebook, Twitter, etc. or can federate users from OpenLDAP, ActiveDirectory.
We will show how Keycloak can be configured to use Github as an external OpenID Connect Provider.
The configuration of a corporate identity provider or other social networks are similar.
This IDP integration on Keycloak could be useful if you want to allow a group of users within e.g. a github organization to login into components provided from kube+ (like Keycloak itself, Grafana, Harbor, etc.). Further permission settings on keycloak like roles and groups are not covered within this How-To.
# Configurations steps
On Keycloak you need to add an Identity Provider. In this case we use Github.
On Github you will add and register an OAuth application using the Keycloak "Redirect URI" value.
As last step you then configure the application metadata in the Keycloak’s Identity Provider.
# Add an Identity Provider
Click on Identity Providers. From the drop-down select GitHub.
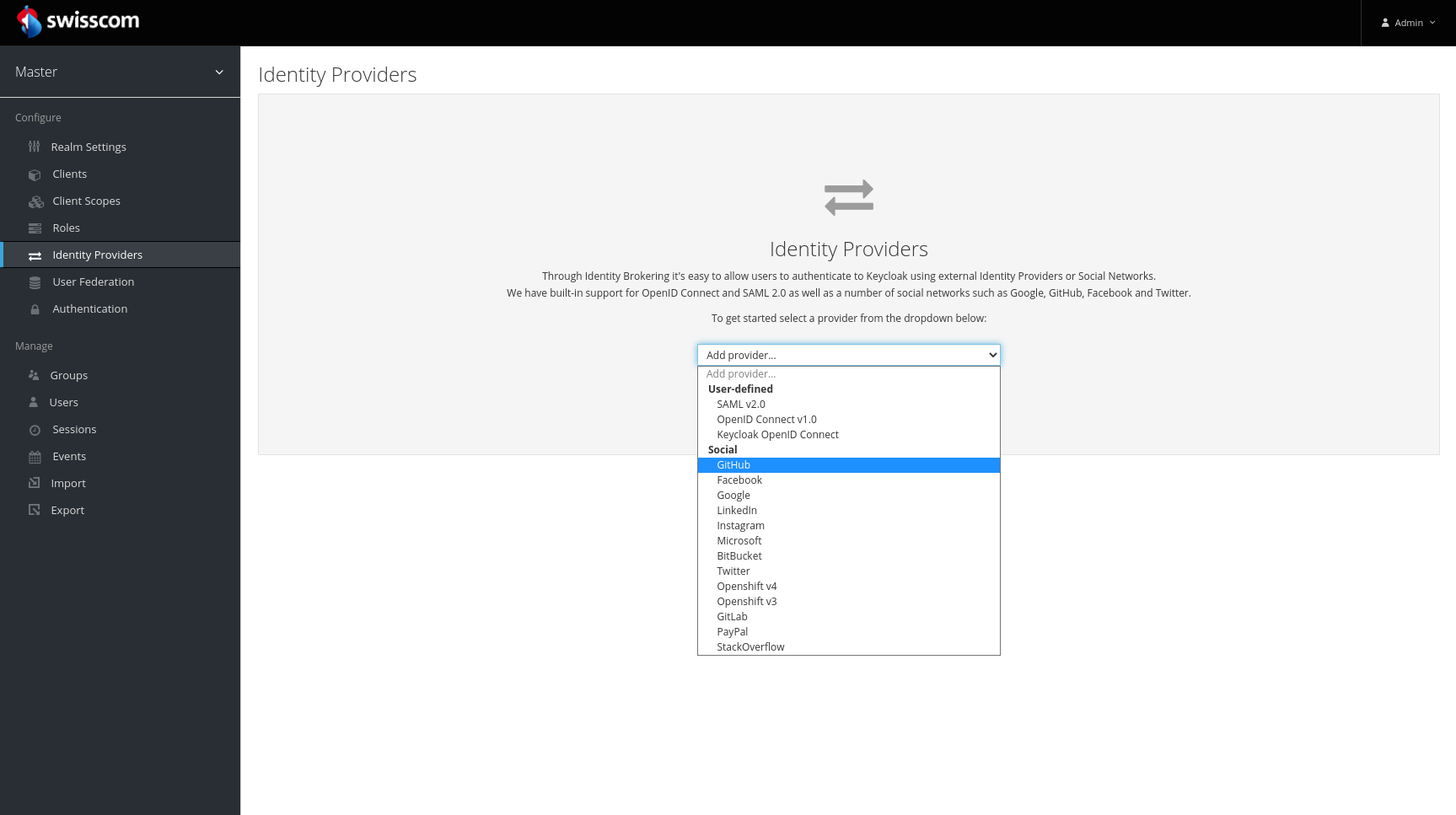
Copy the value from the field Redirect URI.
You'll need this value when you create a new OAuth application on GitHub.
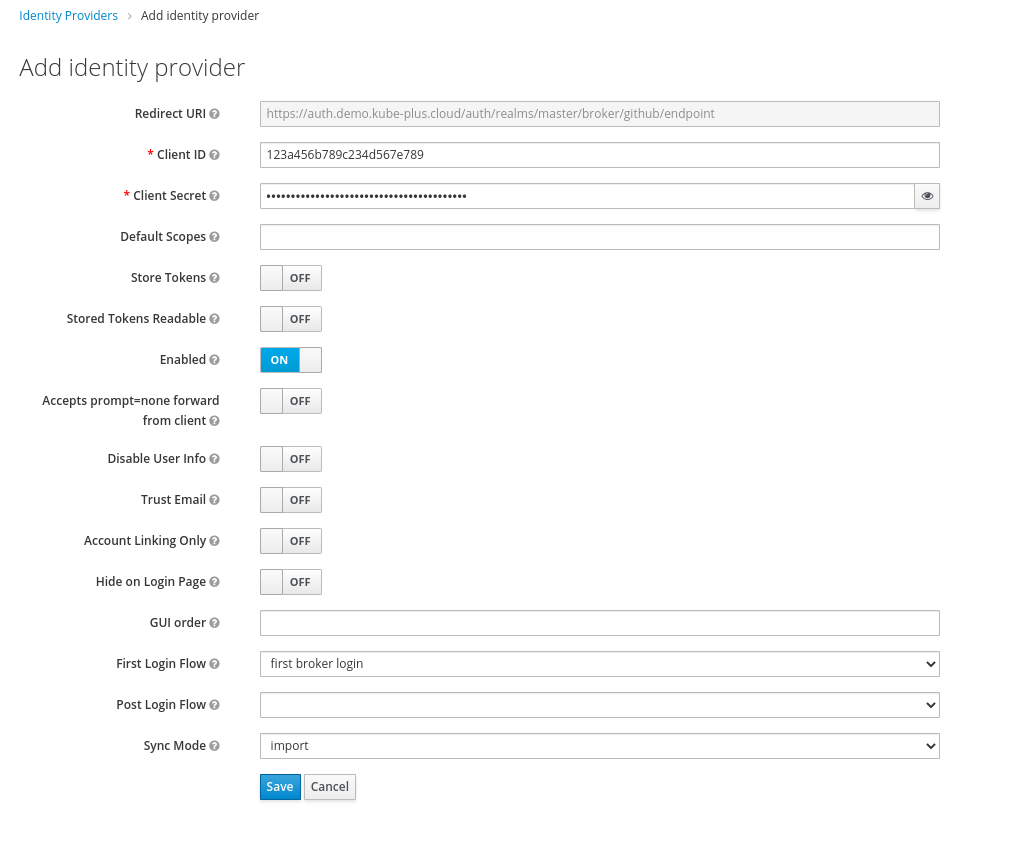
The fields Client ID and Client Secret can be filled with the values provided from the Github OAuth App register step (see further below).
# Github create and register OAuth app
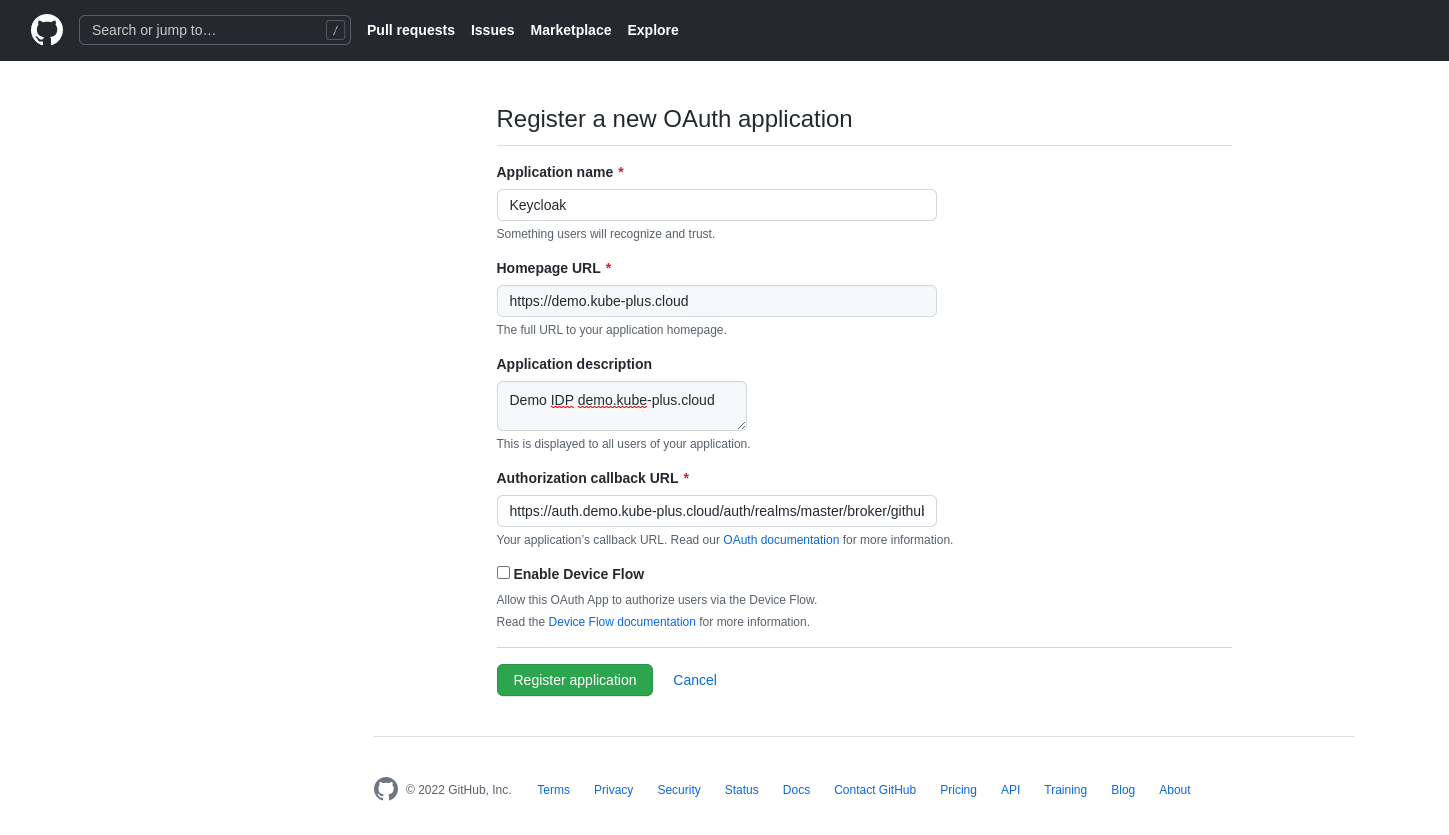
Open the github URL to create and register a new OAuth app under your personal account Github Developer settings (opens new window) or under your github organization https://github.com/organizations/{your_org}/settings/applications/new.
Documentation: Create OAuth App (opens new window)
Fill in the copied Redirect URI from keycloak into the github app register form on the field Authorization callback URL.
Complete the form and register the application.
You will get a Client ID and a Client Secret generated for your registered OAuth application.
Copy these values from GitHub to the Keycloak Admin Console where you setup the Identity Provider.
# Login Screen with IDP
The newly added Identity Provider "GitHub" will now show up on the login page for the used keycloak realm and allows user sign in.
Each user logging into your realm using an external identity provider has an entry in the local keycloak database, based on the metadata from the SAML or OIDC assertions and claims.