# Route 53
In order to be able to access the kube+ system components and your user applications you need to setup a CNAME-Record for the system_domain in Route53.
# System Domain
# Create the CNAME-Record
- Go to the AWS Console Dashboard and choose Route53
- Go to the Hosted Zone where you manage your DNS records
- Click Create record and select the following values:
- Record type: Select CNAME
- Record name: Type the specified wildcard entry for the
system_domainfrom your configuration, e.g*.my-example.com - Value: Type the hostname of your elastic loadbalancer of the
system_domain
# Example records
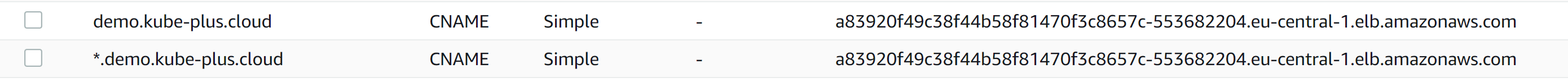
Here is an example of a fully configured kube+ DNS record set on AWS Route53 DNS.
# Test your records
Now it's time to verfiy the CNAME-Record(s) you just created.
Test the system_domain
In our example we defined a CNAME like *.demo.kube-plus.cloud for the system_domain. This CNAME you can now test with an existing kube+ system component like Keycloak (auth):
$ dig auth.demo.kube-plus.cloud
; <<>> DiG 9.18.1-1ubuntu1.1-Ubuntu <<>> auth.demo.kube-plus.cloud
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 14917
;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;auth.demo.kube-plus.cloud. IN A
;; ANSWER SECTION:
auth.demo.kube-plus.cloud. 600 IN CNAME af95b61f466334e529b6632affb50f52-1313892485.eu-central-1.elb.amazonaws.com.
af95b61f466334e529b6632affb50f52-1313892485.eu-central-1.elb.amazonaws.com. 60 IN A 3.65.66.98
af95b61f466334e529b6632affb50f52-1313892485.eu-central-1.elb.amazonaws.com. 60 IN A 3.64.34.26
af95b61f466334e529b6632affb50f52-1313892485.eu-central-1.elb.amazonaws.com. 60 IN A 18.156.124.249
;; Query time: 232 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Tue Jun 07 13:08:36 CEST 2022
;; MSG SIZE rcvd: 190
# Programmatically add DNS entries
The following section displays example scripts to programmatically add the necessary DNS entries.
NOTE: Make sure your are logged into AWS.
NOTE: Make sure your are logged into the correct k8s cluster before you execute the shell script and
kubectlcommands!
To add the CNAME system_domain DNS record, use the shell script below.
system_domain DNS entry (Click to expand)
# setup route53 entries on AWS
export HOSTED_ZONE=$(check the config property aws.route53.zone in the config.yml)
export SYSTEM_DOMAIN=$(check the config property system_domain in the config.yml)
if [ -z "${SYSTEM_DOMAIN_LB}" ]; then
export SYSTEM_DOMAIN_LB=$(kubectl -n contour-external get svc/envoy -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')
fi
# echo "SYSTEM_DOMAIN [${SYSTEM_DOMAIN}] LoadBalancer: ${SYSTEM_DOMAIN_LB}"
sed "s/:SYSTEM_DOMAIN:/${SYSTEM_DOMAIN}/g; s/:SYSTEM_DOMAIN_LB:/${SYSTEM_DOMAIN_LB}/g" route53-upsert.json.tmpl > route53-upsert.json
# echo "applying route53 entries ..."
export APPLY_CHANGE=$(aws route53 change-resource-record-sets --hosted-zone-id "${HOSTED_ZONE}" --change-batch file://route53-upsert.json)
sleep 30
#echo "querying route53 ..."
export CHANGE_ID=$(echo "${APPLY_CHANGE}" | jq -r '.ChangeInfo.Id')
aws route53 get-change --id "${CHANGE_ID}"
aws route53 list-resource-record-sets --hosted-zone-id "${HOSTED_ZONE}" --query "ResourceRecordSets[?Name=='\\052.${SYSTEM_DOMAIN}.']"
- Check out this config property for the
aws.route53.zone. - Check out this config property for the
system_domain.
